Daas Desktop As A Service for Beginners
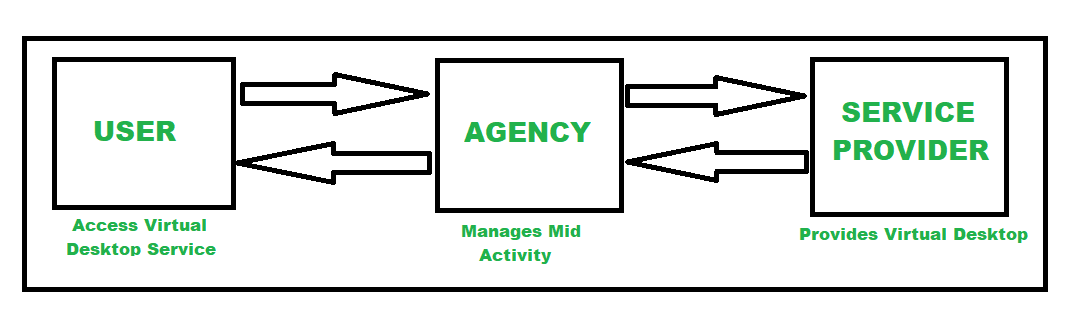
The Daa, S service provider after that streams the virtual desktops to the client's end user gadgets. Daa, S service providers handle the VDI release as well as maintenance, protection, upgrades, information backup, and storage space.
What is Daa, S (Desktop-as-a-Service), and also just how does it contrast to digital desktop framework (VDI)? The tech world is widely known for being a maze of acronyms. You may have become aware of Saa, S, Paa, S, as well as Iaa, S Right here is one you may not be as acquainted with: desktop as a solution or Daa, S.
Not known Facts About Daas Desktop As A Service
7% between 2019 in between 2026As well as Daa, S stands for desktop computer as a service. It refers to a form of digital computing that supplies remote or mobile workers with cloud workspaces. Making Use Of Daa, S, workers can link to a virtual workspace that runs in the cloud utilizing whatever tool they have.
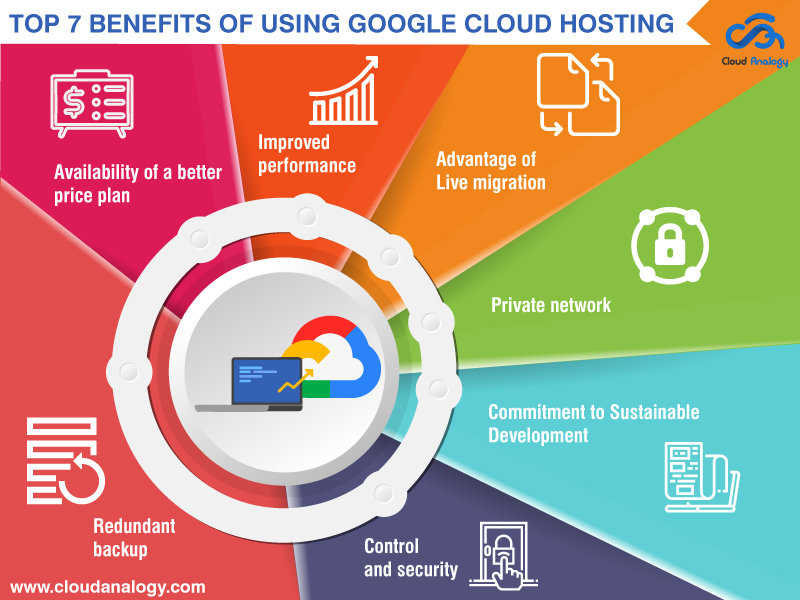
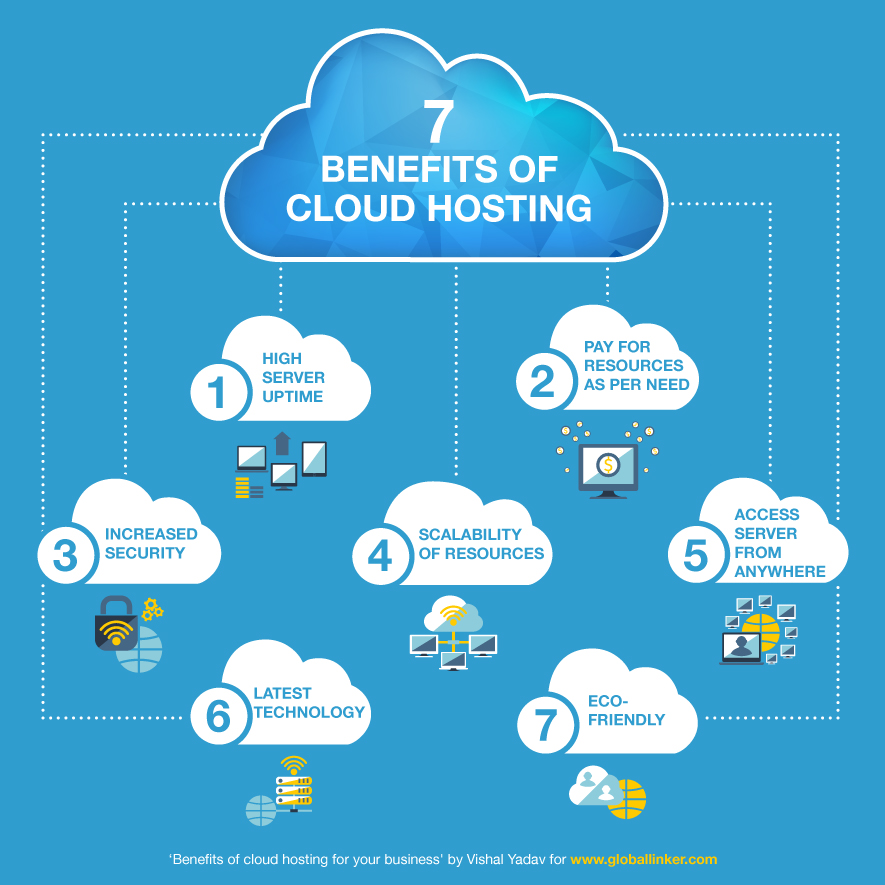
A current record by the Citrix Provider Of Quality revealed that the Daa, S market has actually "matured as well as advanced" in current years. The primary benefits of desktop as a solution are: Adaptability, Lowered upkeep prices, Security, With Daa, S, companies can provide a work space to brand-new employees without having to bother with provisioning equipment or bothering with specific configurations.
He notes "Secure digital desktop facilities (VDI) as well as desktop-as-a-service (Daa, S) connections have ended up being a top priority over the last two years, given the rapid development of virtual meetings, remote training sessions, and also sales telephone calls. VDI/Daa, S aids protect against online sessions from being hijacked while safeguarding the identity of every virtual participant without any deterioration in data transfer."Using Daa, S means companies can execute Bring Your Own Device (BYOD) plans published here as well as permit employees to function from anywhere.

The 9-Minute Rule for Daas Desktop As A Service
The digital machine is reset when they log out. This restricted accessibility cuts off numerous typical assault vectors that are open on standard desktop computers. Somehow, Daa, S may appear a lot like online desktop computer facilities (VDI). Those comparisons are reasonable ones. However, there's one key distinction in between Daa, S as well as VDI.With VDI, companies use on-premise web servers that are preserved by in-house groups.
They're also in charge of safety monitoring as well as upgrades. For lots of companies, the expense of managing that infrastructure in-house is too high. Daa, S utilizes cloud-based digital desktops. This suggests companies can make use of a third-party hosting carrier that manages the equipment, networking and software application for them. To the end-user, the result coincides. DAAS Desktop as a Service.
"Digital desktop framework is given via on-site technology solutions and also calls for an equipment pile preserved by IT administrators. Heritage VDI services are intricate devices (DAAS Desktop as a Service).
This figure takes right into account the cost of getting and also implementing all of the required framework. One of the most significant advantages of including a Daa, S version is cost-saving. With heritage IT, organizations have to acquire a perpetual permit for every desktop computer as well as every laptop computer in operation by the business.
The Best Strategy To Use For Daas Desktop As A Service
Daa, S additionally conserves companies money on safety and security, technological assistance, and also upkeep., included that a Daa, S system this article can be "easily and quickly" provisioned to meet your demands.
Short-term workers can be appointed logins and also have those credentials withdrawed when they leave the business. Several companies supply adaptable rates.
— Cloud Links (@ldcloudlinks) December 14, 2022
Plus, you don't have to worry regarding hardware failing, merely because the system is cloud-based. For an organization that has a mixture of office-based as well as remote workers, managed cloud solutions as well as remote desktop computers can be an effective source. They make it possible for remote workers to log in to a safe setting where they have accessibility to every one of their productivity apps click and info.
There's no need to invest a great deal of money on expensive equipment to access their systems. Purchasing a Daa, S solution can be cost-effective for many firms, however the wrong service can cause higher-than-expected costs, as highlighted in this research by Business Strategy Group. Consequently, it's essential to pick a Daa, S provider that provides transparent rates that makes sense for your use instance.